New Security Features for Azure/Office 365
Security Defaults are being enabled by Microsoft for some existing customers. What does this mean for your business?
In the summer of 2022, Microsoft announced the rollout of security defaults to existing customers (some 60 million of them) who use their Microsoft Azure service. It was designed for tenants which do not utilise a feature called Conditional Access, which allows deep customisation and security to the login experience to be set.
The value of this being enabled is for companies with limited IT resources that would benefit from an automatic tune up of their security.
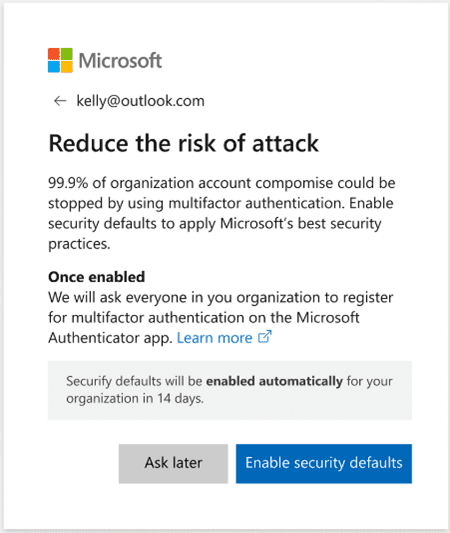
What does this mean for us?
If you’re using conditional access, you are not impacted by these changes. If however you don’t use it, the following features will be automatically enabled:
- MFA (or multifactor authentication) will be enabled. This feature requires a user to further identify themselves by using an additional method above a username and password such as an authenticator app or mobile number to receive an SMS. According to Microsoft, 99.9% of compromised accounts were due to them not being protected by this feature.
- Administrators will have to use MFA every time they sign in.
- Disabling legacy forms of authentication that don’t support MFA. Some environments use old methods of transmitting or receiving email using protocols such as (SMTP, IMAP and POP3) which will stop working after this change.
How can we prepare?
If you’d like to discover the extent of users logging in with legacy authentication, you can do so from https://portal.azure.com > Azure Active Directory > Sign-ins and in the filters area, select the types from the legacy authentication clients section. The list can then be downloaded to excel for easier analysis depending on the size of the results.
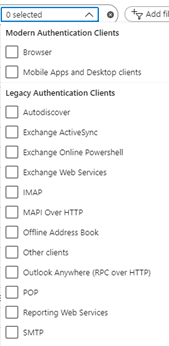
From there, identification of users/services that need to be resolved can begin. Examples may be upgrading user phones that have old mail clients on them, through to changing applications using SMTP services to use secure protocols.
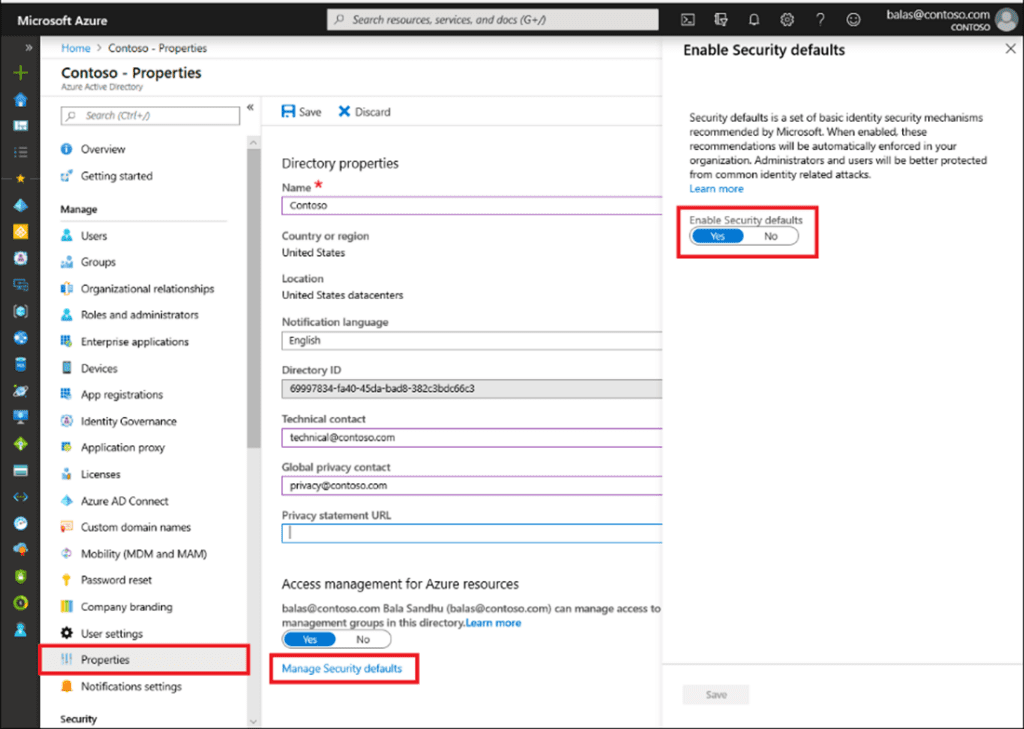
If this has been enabled and you need to switch it off, there is a way! In your Azure (https://portal.azure.com) portal, Browse to Azure Active Directory > Properties Select Manage security defaults > Set the Enable security defaults toggle to No.
If your business needs help, Ultima can provide advice and assistance getting your environment ready for a more secure configuration.




