How to deploy a multi-layered data protection and recovery solution with CommVault
Reducing cybersecurity risk and ensuring data availability through secure backup is a priority to any organisation. NIST have defined a Security framework which guides customers in the following of five pillars:
- Identify - Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
- Protect - Develop and implement appropriate safeguards to ensure delivery of critical services.
- Detect - Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
- Respond - Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Recover - Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
This end-to-end framework consists of feature sets, guidelines, and best practices. Providing your organisation with the best recovery capabilities is the ultimate goal.
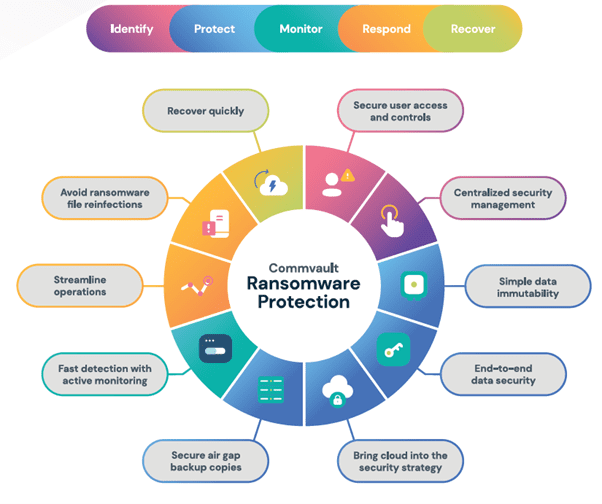
Source: CommVault
The approach in detail
Security-conscious organizations like yours can trust Commvault on data recovery and get the businesses back up and running in no time. Through our multi-layered security approach to data protection and management, your organisation benefits from the below.
| Identify | Secure user access and controls | AAA Framework protects who has access and what they have access to while monitoring events and activities for proper security. Link |
| Centralized security management | Single pane of glass to centrally monitor, manage, and adjust the security levels and parameters. Link | |
| Protect | Simple data immutability | Protect against changes from inside and outside the backup solution. Restore unchanged and unmodified backup data anytime. Link |
| End-to-end data security | Data is encrypted at the source, in flight, and at rest using industry-standard protocols with multiple options for key management and interoperability. Link | |
| Bring cloud into the security strategy | Metallic Cloud Storage Service makes it simple to securely adopt cloud storage and ease digital transformation. Link | |
| Secure air gap backup copies | Isolate and segment storage targets from public networks to mitigate lateral moving threats. Link | |
| Monitor | Fast detection with active monitoring | Use machine learning, artificial intelligence, and honeypots to monitor and detect suspicious or unusual activity for greater insights and faster time to recovery. Link |
| Respond | Streamline operations | Coordinate interactive responses and actions using APIs, workflows, and integrations with external orchestration platforms. Link |
| Avoid ransomware file reinfections | Ensure a clean and secure recovery by surgically deleting suspicious files, unnecessary files, or creating an isolated recovery. Link | |
| Recover | Recover quickly | Minimize lost revenue with fast, flexible cloud, virtual, and on-premises recovery options. Link |
Ultima complementary services
With over 20+ years of IT consulting experience with the highest levels of customer satisfaction, we have become trusted advisors and the ideal technology partner for many. With our expertise we can offer a comprehensive set of services with our partners to protect and add value such as:
- Advisory Services to provide strategic services to identifying key data assets, developing key requirements, comparing features with industry practices, recommendations towards a new target state and strategy.
- Delivery of Design & Deploy services to ensure the solution is implemented to best practices.
- Migrate and Operate to transition to your staff to enable them to manage and run the new solution.
- Fully manage and support 24/7 services that you can depend and rely on.
How Can We Help?
If you would like to learn more about how Ultima can support with your ransomware protection, we are offering you a free consultation to discuss how you can secure & protect your backup data to mitigate risks from a ransomware attack.




