Cloud Security: A potential management nightmare?
Talking to one my industry colleagues over a virtual beer during one of the lockdown phases, we got onto the subject of security; specifically, when you’re managing a system that is mainly one, or a few key vendors in terms of software and service, how do you manage the ever-changing world of security issues? How do you know when there are vendor-based problems or that someone internally hasn’t accidentally mis-configured something? With potentially hundreds of components and settings and multiple changes it’s a security departments worst nightmare!
Because of this, we sat down and mapped out 3 key areas to consider when security comes into play in the cloud.
Exploits are on the rise
For those not in security circles, when vulnerabilities are discovered one of the major sources that identifies, confirms, and publishes findings is the Common Vulnerabilities and Exposures (CVE) system, operated by Mitre Corporation. This is also in conjunction with other security industry services such as the National Vulnerability Database (NVD) and the National Institute of Standards and Technology (NIST). While pre-dominantly US based, these are a globally recognised services for security in the IT industry.
So why are we referencing this? Well, it’s to review just how vulnerabilities have changed and grown over the last few years. Let’s take Microsoft, as a major key vendor, as an example of any vulnerabilities published for any of their software and/or services.
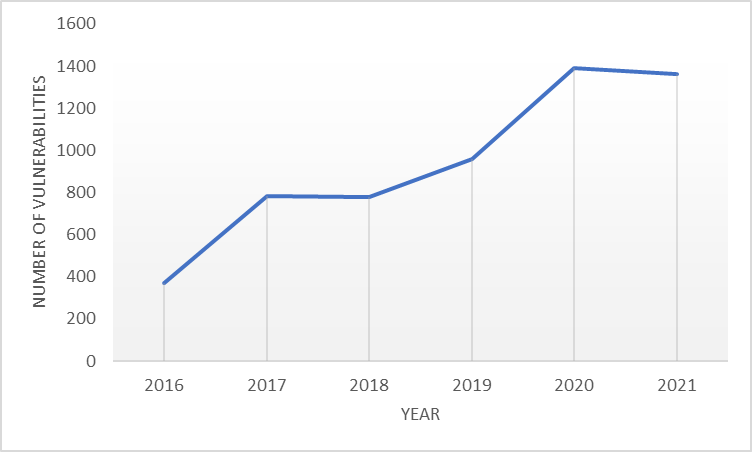
So, the number of vulnerabilities doubled between 2016 and 2018 and have practically doubled again a few years later. We’re now at a point of averaging 4 vulnerabilities on this vendor alone every day. This is not to paint Microsoft in any negative light, as many other major vendors are also having similar challenges. The CVE database has a list of over 168,000 known vulnerabilities across all vendors, services, systems etc. so, this is an ever growing problem to keep on top of.
The cloud moves 3 times faster than on-premises
As more customers transition into the cloud for applications and services, the rate of change accelerates. This isn’t just new features or changes to services but also how customers procure, change or configure their services, as the cloud often opens up much greater scale, flexibility and overall number of services compared to what is available from on-premises, which is great for businesses and their staff.
To give this some context let’s take Microsoft’s DevOps service, which was formerly called Team Foundation Server (on-premises). This is now available either as a cloud SaaS service or you can run an on-premises version of the software yourself. For a time at least when updates were made available, the SaaS based solution would have these available every 3 to 4 weeks, where the on-premises version would be every 3 months.
So, what does this mean from a security perspective?
With new capabilities and features being added all the time, the chance of misconfiguration or drifting from security best practice increases over time, especially when we talk about your technical skill resource capacity available. Speaking of that…
A skills shortage creates a perfect storm
With the rapid rise in cloud technology, a rise in security challenges and a faster pace of change, delivering a safe, secure and modern service can be hindered by a lack of available skilled workers in these areas.
In 2021 Gartner reported that the cloud skills shortage was impacting cloud adoption by as much as 64%, a significant increase over previous years as businesses look to utilise the scale, flexibility, and speed of cloud computing-based services*.
This means that from a security perspective, there is a high degree of certainty that cloud adoption or general cloud management is not being done to security best practices, or that the high rate of change where technical staff are not adequately experienced can only heighten potential security risks due to implementation mistakes or ongoing accidental misconfiguration.
To give this some context, Gartner estimates that up to 95% of cloud-based security breaches were due to human error, such as configuration mistakes**.
**https://www.wsj.com/articles/human-error-often-the-culprit-in-cloud-data-breaches-11566898203
This makes it incredibly difficult to keep on top of changes that you are implementing to your services and trying to review your configurations and best practice stance can be a long, painstaking task.
Conclusion
Managing exploits of your key vendors and tracking infrastructure changes that could impact your overall security posture are key areas going into 2022. The more you change, the more services you use, the harder it will be to keep track of the ever-evolving security landscape.
Your staff too will need to adapt, and with the cloud skill shortage still a problem, your existing staff will need training up and enabling in terms of analysing potential security issues with your cloud infrastructure.
How IA-Cloud can help
With the rise of vulnerabilities, a faster rate of change and a lack of skills, there needs to be a way to combat these problems.
IA-Cloud is our automated management, monitoring and optimisation platform for your Microsoft Azure workloads. As part of IA-Cloud and through our cloud technical experience, security plays a bit part in overall management.
To help combat and improve your security stance for their cloud services, IA-Cloud now offers security compliance that has been simplified to help you to understand your security posture and make easy-to-review improvements. This means an automated, central place to review any issues without having to keep track of every single component and work task.
IA-Cloud will scan your Azure environments every week and highlight where infrastructure security could be improved or where potential misconfiguration has occurred, all through automation. The service provides these explanations in “plain English” that leads itself to assist in understanding how remediation can be applied. All the recommendations are based on industry standards such as a Centre of Internet security (CIS, a derivative of NIST) as well as our own combined decades worth of cloud consulting experience.
And when it comes to vulnerability management, IA-Cloud also has this covered. IA-Cloud’s security compliance includes a vulnerability scanner service that automatically gathers published Microsoft vulnerabilities from the past 2 weeks with urgent criticality and transforms the results to make it as simple to follow and remediate as possible, all in a centralised pane and completely automated. This includes the description, related technologies and even a remediation report, assisting you in preventing potential exploitation without wasting time and resources on information gathering.
There’s so much more to the tool, so why not find out about IA-Cloud




